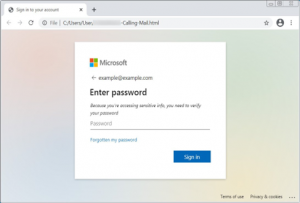
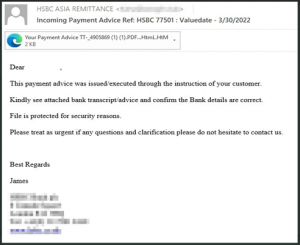
True story: At a company I once worked for, employees received an email about an unexpected bonus. In private Slack channels, we wondered whether it was a well-played phishing attempt. Turns out, the bonus was legit, but so was our inclination to question it. Phishing—when cybercriminals pose as legitimate institutions to get info or money from you—is the origin of up to 90 percent of breaches and hacking incidents, says Frank Cilluffo, director of Auburn University’s McCrary Institute for Cyber and Critical Infrastructure Security in Alabama.
These cyber bad guys have even taken it to the next level with “spear phishing,” a practice of sending emails that appear to be from someone you personally know. “This happened to me once and it was a humbling experience,” says Adam Doupé, director of the Center for Cybersecurity and Digital Forensics at Arizona State University in Tempe. Turns out, the email seemed to be coming from a colleague, and Doupé was boarding a plane when he got it so he wasn’t as careful as he would normally be. “I ended up replying with my cell phone number,” recalls Doupé. “When the phisher responded with a request to send gift cards, the alarm bells went off.”
Knowing that a cybersecurity expert got played, an average person has to be hypervigilant. But could you be missing out on legit offers and emails because you’re being too cautious? Your first line of defense: install a protection software (like Malwarebytes). This sort of protection that lives on your computer, coupled with our expert tips below, will stop phishers in their tracks.
3 Ways To Tell If It’s Phishing Or Not
Experts say there are a few things you can do if you’re unsure whether an email is a phishing attempt.
1. Check the email address carefully.
Hover your cursor over the full email—not just the sender’s name—to see if anything looks off. “For instance, instead of .com, the address may contain .ru,” says Cilluffo. (.Ru indicates that it’s from a Russian server.) Compare the address on a recent email to one that you’ve responded to previously.
2. Call or text the person you think may have sent the email.
Ever receive an email from a friend or colleague and it seems off? Maybe it’s much briefer than usual or perhaps they addressed you by your full name rather than a nickname. Trust your gut, and don’t respond or click on any links or attachments until you’ve verified the email. While it truly may just be a link to their kids’ fundraiser, it could be the work of a cyber criminal trying to get you to download malware—aka malicious software.
3. Verify through an independent news source.
Sometimes you may receive an email about an important recall notice or info about a class-action lawsuit. Search on a trustworthy news site whether the link contained in your email appears in any news articles, suggests Doupé.
Bottom line?
Cyber criminals are getting more and more creative at making their phishing attempts appear legitimate. Go with your gut, slow down to verify the validity of messages you receive and install a protection software (like Malwarebytes) to stop phishers before they start.
Are you interested in learning more about cybersecurity? Call us today and discover how our wide array of tech services can safeguard your business.
If you are looking for an expert to help you find the best solutions for your business talk to GCInfotech about a free technology assessment
Published with consideration from yahoo.com SOURCE